Solutions
Automate Cloud Infrastructure Provisioning with Chef Terraform Provisioner
Ensure Consistent Deployments in Any Cloud Using Chef and Terraform Together

What is Hashi Terraform?
Hashi Terraform is an “Infrastructure as code” (IaC) framework that automates infrastructure provisioning across providers and cloud environments. It enables Infrastructure automation using a declarative configuration language designed for
cloud-agnostic abstraction. At a high level, Terraform combines a library of providers, responsible for defining interactions with specific clouds’ APIs, with provisioners, responsible for defining how infrastructure should be configured once
they’re launched.
Expressing infrastructure as code makes it easier to automate infrastructure provisioning at scale. This approach not only helps with disaster recovery but also makes testing and development processes less complicated. Terraform
works with Manifest files which define the type and the count of resources that need to be deployed. Terraform uses these Manifest files to create the required infrastructure in the cloud as described in the manifest.
System Configuration vs. Provisioning

What is Provisioning?
The process of creating and setting up infrastructure resources is called provisioning. These could be servers, databases, load balancers or virtual machines. Once a resource has been provisioned, it requires configuration. Terraform is an example of a provisioning tool.

What is Configuration Management?
The process of defining and maintaining systems or software in a specific state is called configuration. IT resources need to be configured to deliver consistent performance, the process may include installing new software packages or maintaining the existing configuration. Chef is an example of a configuration management tool.
Provisioners are a type of resource that needs to be managed - either provisioned or created like virtual machines and machine images. Terraform was designed for three generic provisioners - file, local-exec, and remote-exec. These provisioners can handle
everything from running tasks on the Terraform worker to running on a remote system or even do file manipulations.
Terraform creates cloud or virtual servers using provisioners such as Chef Infra Provisioner to enable configuration management. When Terraform talks to APIs to define or configure resources, it uses Providers such as the Chef Infra Provider
to request those resources.

Automate Infrastructure Provisioning with Chef and Terraform
Chef’s comprehensive infrastructure automation stack works seamlessly with Terraform to extend its provisioning capabilities.
Organizations can set up IT environments quickly combining configuration and provisioning tools. Chef offers extensibility that makes it easy to integrate with tools such as Terraform and manage the entire infrastructure workflow.
Chef Infra Provisioner
The Terraform Chef Provisioner bootstraps Terraform, provisioned with Chef Infra via SSH or WinRM, and configures them to work with a Chef Infra Server. Standard bootstrap options such as Chef Infra versions, secrets, proxies, and assigning run lists via Policyfiles or Roles and Environments are all supported.
Chef Infra Provider
The Terraform Chef Provider allows you to manage Chef Infra Server resources (nodes, data bags, etc.) using the Chef Infra Server API.
Additional Chef-Terraform Integrations
- The Habitat Provisioner may be used to install and load the Chef Habitat Supervisor and configure the services to be managed by the supervisor.
- Kitchen Terraform is a community Test Kitchen driver that allows for multi-node testing.
- InSpec-Iggy is a community InSpec plugin that generates InSpec compliance controls and profiles from Terraform tfstate files and AWS CloudFormation templates.
Testing Terraform with Kitchen and InSpec
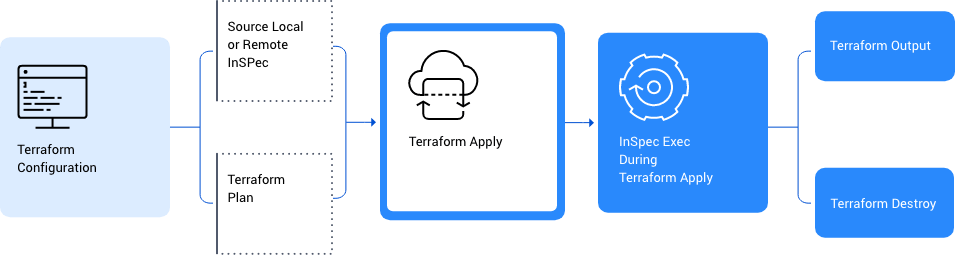
The Chef provisioner plugin can be executed during a Terraform run to validate the state of virtual machines and cloud infrastructure in a single operation. Include InSpec Exec resource actions within Terraform plan configuration to perform testing during the apply process and optionally halt/destroy based on results of InSpec scan. In addition, Inspec-Iggy (“InSpec Generator,” or I.G.) enables users to generate compliance controls from a Terraform state file.
Additional Resources



