Deconstructing Compliance and Security – How is it Different?

In the world of ITOps, a discussion on security is inevitably followed by a discussion on compliance. Security and compliance are, by default, considered complementary - both are essential in reinforcing cybersecurity and minimizing risks/vulnerabilities.
The IT operations team in an organization works towards securing infrastructure and critical assets, but this does not mean that compliance is guaranteed. An organization can be secure but non-compliant or even vice versa. Such scenarios happen when there is no clear understanding of the need for security and compliance, how to achieve both, or when one is prioritized over the other in justifying key asset protection.
This blog discusses how compliance and security differ and how Chef can help you achieve compliance while maintaining a secure infrastructure. But before we talk about the differences, let us align our interpretation and what these two terms entail.
What is IT Security and Compliance?
IT Security can be defined as a set of rules and regulations implemented by an organization to govern accessibility and to protect the integrity and confidentiality of critical business assets. For example, when implementing authentication mechanisms to secure access to business assets. The aim is to “harden” system integrity, deter infiltration and reduce the impacts of cybersecurity compromise.
IT “Compliance” shares many of the same goals as “security” in protecting digital assets. But how it is implemented and assessed is typically based on a regulatory framework. The framework can be defined either by internal policies or by a third-party regulatory body. So, “Compliance” can be defined as the process of meeting specific standards/requirements and pre-requisites that enable secure business operations.
Both of these IT components manage risk, but they differ in action. The security team in an organization spends time building and configuring a secure architecture that can protect, detect and prevent security threats. The compliance team deals with risk management through policies and regulations that ensure the organization complies with the stipulated framework.
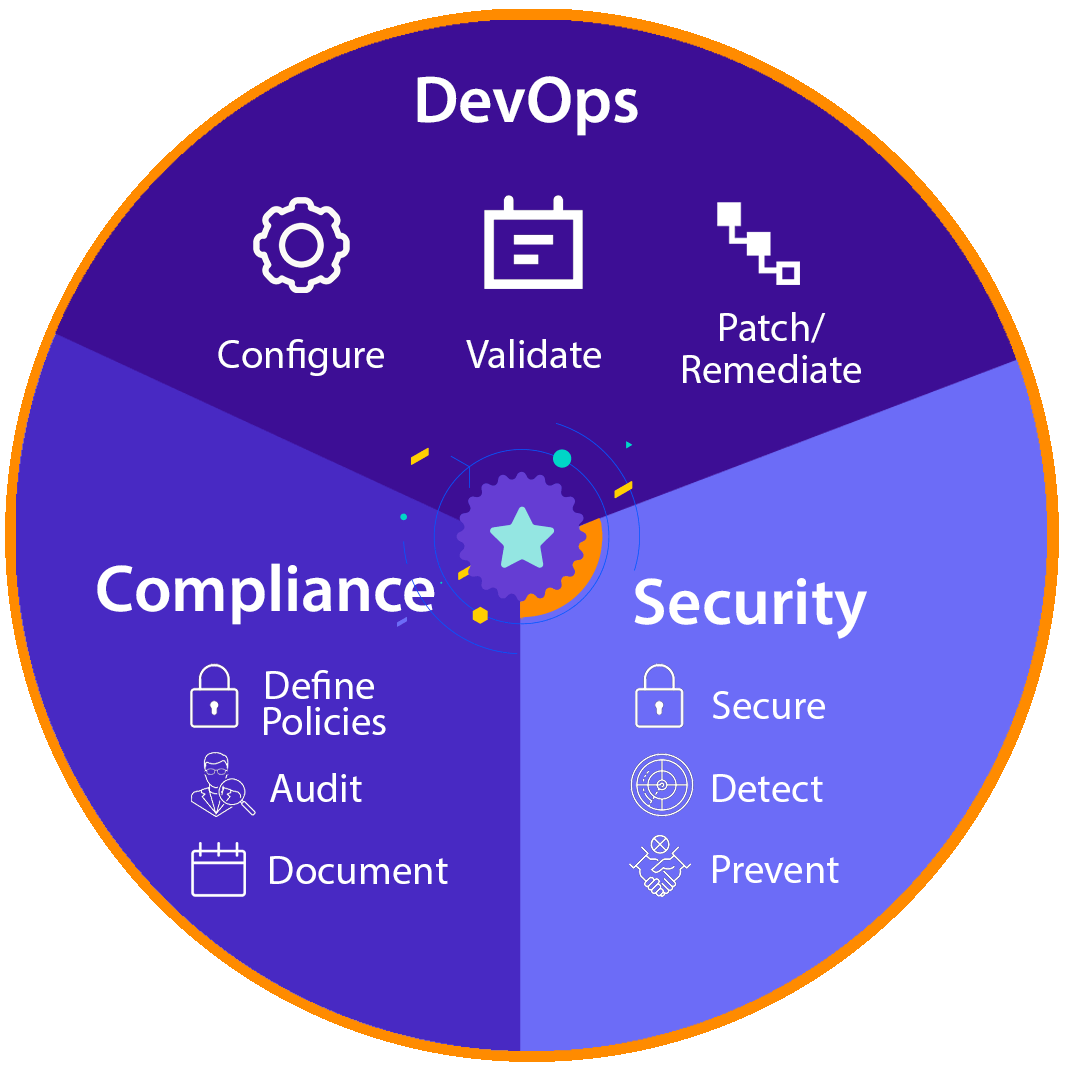
Security – secure, detect, prevent.
- Build and implement a secure infrastructure.
- Detect and prevent security threats.
- Must be continuously maintained and upgraded for system hardening.
- It is a critical technical requirement for security business operations.
Compliance – secure, audit, remediate.
- Define policies based on third-party requirements.
- Ensure business operations comply with internal policies.
- Requires updates only when regulations change.
- It is a critical business process to maintain a state of compliance.
DevOps – configure, validate, patch/remediate
- Configure systems based on defined business policies
- Test systems and validate state across environments
- Patch and remediate vulnerable systems
- It is a critical technical requirement for running business systems.
Managing Risk Through Automation
DevOps practices bring together different teams and tools to deliver reliable software. Security has always been integral to DevOps and the software delivery lifecycle, but it is usually overlooked, deprioritized, and only implemented in the very last stage of the delivery phase. This is because integrating security and compliance practices has been a tricky business for IT teams. Minimizing risk typically means compromising release velocity and agility. The DevSecOps approach introduces security and compliances practices at every phase in the SDLC, allowing development, operations, and security teams to collaborate more effectively.
Automating the security and compliance processes can significantly reduce the complexities of scale and infra diversity. Replicating tested and verified processes across the entire organization is the first step towards automation, and the most reliable method of building reusable processes is through code. Codifying these processes will bring consistency across the organization; it simplifies time-consuming steps and minimizes human error.
Chef offers solutions that break down complex processes into code that is traceable, auditable, and easy to scale. This approach makes security and compliance processes less formidable, more manageable, and easily integrated into every phase of the software development cycle.
Chef Compliance Automation for Secure Infrastructure Management
IT teams deal with a range of controls to limit vulnerabilities and secure their infrastructure and endpoints. This includes fluid changes in corporate security policy, consistently monitoring security breaches, and proactively preventing intrusions. It is vital to manage infrastructure configuration and logs so that every system is secure and aligns with the organization's overall security posture. Chef automates configuration management and validation, allowing all resources to be evaluated and updated consistently and continuously.
Chef Compliance Automation for secure infrastructure –
- Defines policies and system configurations as code to integrate with automated pipelines.
- Detect and correct configuration drift to ensure the entire infra is in the desired state.
- Manage diverse systems irrespective of OS.
- Maintain security and compliance with minimum effort.
- Allows security and compliance to shift-left, increasing release velocity.
Chef Compliance Audit for Hybrid and Multi-Cloud Environments
With organizations moving to the cloud, clusters of systems on different networks need to be configured, maintained, and monitored. Auditing such a large and disparate set of systems is time-consuming, complex, and error-prone. It is a herculean task to ensure consistent compliance.
Chef offers a comprehensive compliance solution that streamlines the process of auditing compliance across the organization’s diverse IT real estate. DevOps and infrastructure teams can leverage Chef Infrastructure Compliance to audit the system’s configuration and compliance posture. IT audit teams can also run automated compliance checks that leverage CIS benchmarks and DISA-STIG content to meet compliance requirements.
Chef Compliance Audit for Hybrid and Multi-Cloud Environments:
- Automates compliance for faster audits and remediation.
- Enables continuous compliance across the entire IT infrastructure and resources.
- Detects non-compliant systems, applies waivers, and updates controls as needed.
“We use compliance as code as a vehicle to unite all of our stakeholders. Scaling beyond humans with compliance-as-code saves you and your system owners time, but auditors should also understand the time savings they are going to gain.” - Kyle Harper, Lead Engineering Manager, Cerner
CONCLUSION
Organizations implement security and compliance to secure critical business assets and prevent intrusions. Compliance and security are mutually inclusive, going hand in hand with one another. The security team implements controls and regulations which are validated and maintained by the compliance team. An efficient and effective DevOps strategy must prioritize compliance and security requirements to enable continuous delivery and faster release cycles.
Learn more about Chef Compliance and Security here