Federal agencies work hard to provide value to consumers of their services, but in order to deliver updates at the velocity their customers demand, they must ensure their infrastructure is hardened and secure throughout the software development lifecycle. Chef Software, for over a decade, has helped Federal agencies automate how they build and manage this ‘infrastructure as code’ (IaC).
A critical component for automating infrastructure, particularly in regulated industries, is the ability to automate not only environments’ configuration, but the process of validating that those environments are configured securely. Chef InSpec enables this validation by managing security ‘compliance as code’. In this capacity, the value is achieved by delivering new capabilities while migrating to the cloud, without any negative impact to the Mission, where security of infrastructure and applications is of utmost priority.
In this sector, the risks of a misconfiguration or failed application release have additional non-financial significance, as organizations must adhere to strict regulatory compliance and audits. To mitigate this risk, Federal and Government departments, as well as many private companies who do business with them, must comply with the Security Technical Implementation Guide (STIG) published by the Defense Information Systems Agency (DISA). Organizations must deliver value at the speed of mission. In order to do so, they must bring compliance into their development processes and maintain a state of continuous compliance in order to achieve consistent audit results.
To further enable Federal and Government users who manage their compliance as code, we’ve announced the general availability (GA) release of STIG profiles for Red Hat Enterprise Linux 7 and Windows Server 2016 that are included with Chef Automate. You can view the release notes here.
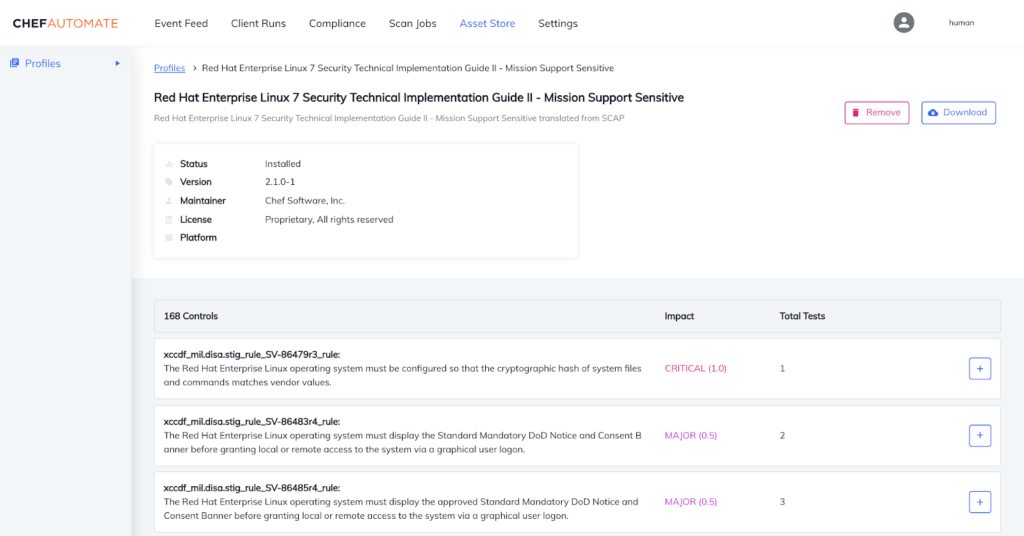
As these profiles leverage the Chef InSpec language, they are easy to read and understand — there’s no need to go through long PDF checklists or obscure XML definitions — and this means your teams (e.g., security, audit, engineers, developers) can work from the same ‘compliance as code’ framework to achieve their shared organizational goals.
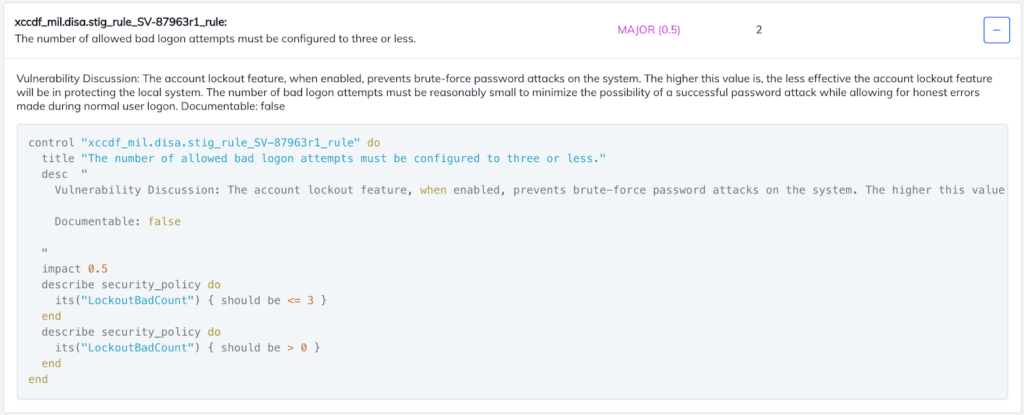
Incorporating these profiles into your development and release workflow will enable all of your team members to iteratively self-evaluate all of your application and/or infrastructure configurations for adherence to the STIG requirements during the development process.
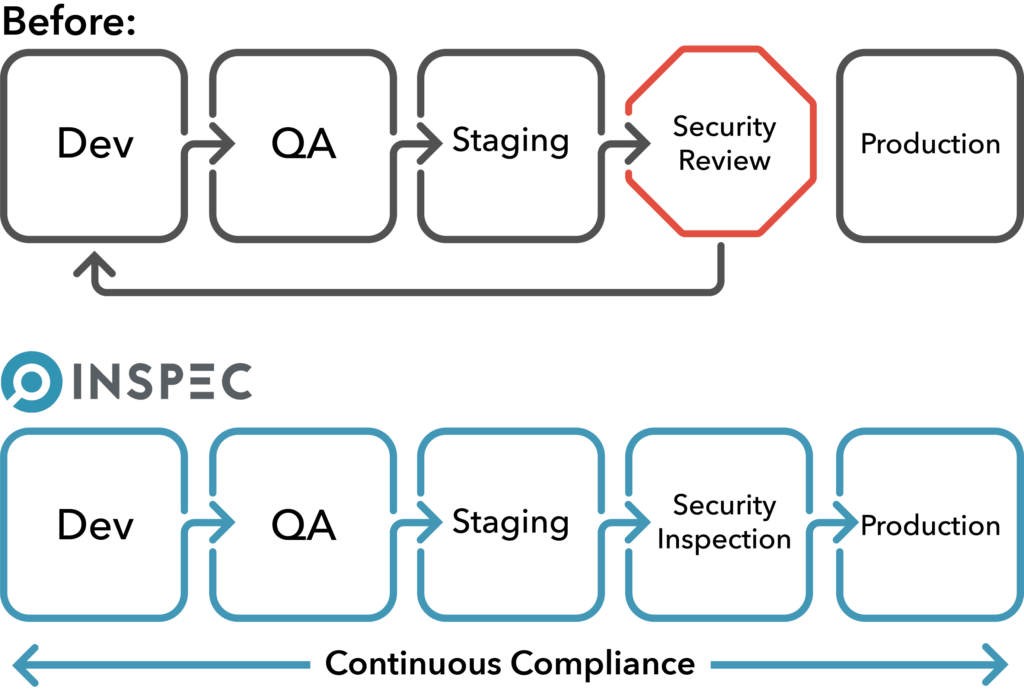
Evaluating security at every stage of development instead of waiting until a change is ready to be promoted to production should become the standard. By continuously auditing for security, deviations from standards are identified and remediated earlier in the development cycle, eliminating costly re-work that would otherwise occur closer to, or even in production. Executing this well defined and efficient process can significantly reduce the amount of time and effort necessary for a release to be approved for deployment, even enabling security teams to automatically approve changes to production.
Adjusting your workflow to apply these activities doesn’t require a dedicated team or significant efforts. The tools all exist within the Chef Automate platform and are well documented. Reviewing and following along with established training modules such as those on Learn Chef Rally will set you on the path to achieving success.
Among these training modules is a recommendation on how to enable specific controls from a compliance profile, such as a STIG profile, that are applicable for your effort. By creating a “wrapper profile” to inherit controls from an existing profile, you can identify individual controls to include or exclude, and even override default values like reported criticality for failures. See this article for more information on creating wrapper profiles.
Once you’ve created a wrapper profile that reflects the particular controls you need to enforce, you’ll want to incorporate it into your local development process. This process, driven by Test Kitchen, will enable you to validate all of your code iteratively during the development cycle.
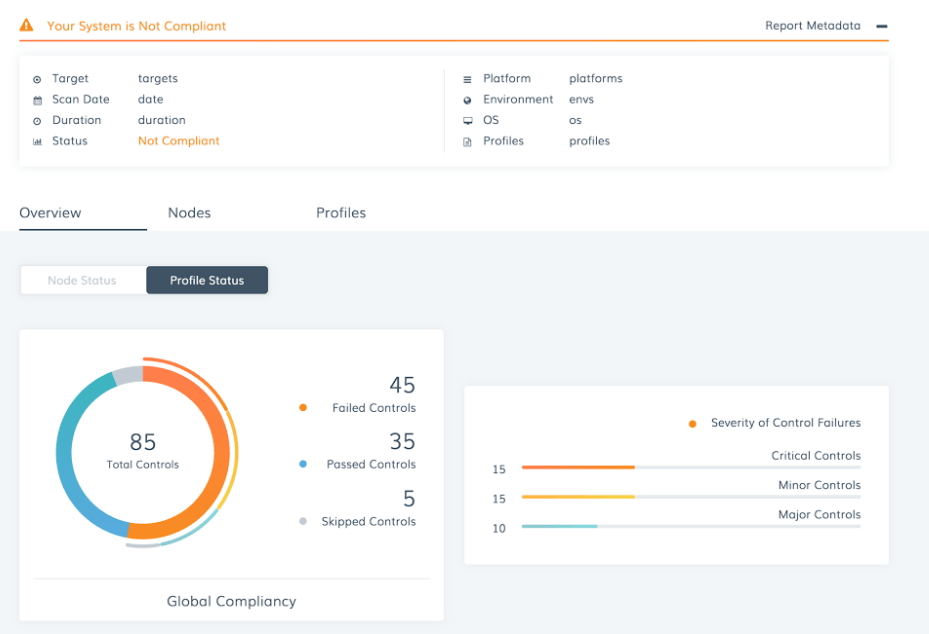
Test Kitchen’s built in InSpec verifier can be utilized to refer to the profiles included with Chef Automate, as well as custom built profiles that may reside in your own Git repositories. If you are not familiar with Test Kitchen, this Learn Chef Rally module will guide you through the local development and testing process.
Lastly, incorporating the continuous execution and reporting of your running nodes against these profiles will help alert you to any changes in your infrastructure that take you out of compliance. The Chef authored and maintained Audit cookbook, added to your nodes’ run lists, will enable this capability and is described in greater detail in this blog post.
By incorporating Chef InSpec into your workflow, you enable continuous compliance, via code. You’ll reduce your risk exposure and bring greater visibility and awareness of your compliance needs to your teams, earlier in the development cycle — which ultimately adds value to the business and your mission.

