Data bags are a great way to store user and application-specific data. Given how users also expect secure storage of passwords and private keys in data bags, Chef offers encrypted data bag items to enable users to put personal data into data bags, reducing the implied security risk.
Before you begin your journey with encrypted data bags, we recommend you go through this blog post on How to work with Chef data bags.
What is Chef Workstation?
To work with data bags, you will first need to download and configure Chef Workstation a collection of developer tools that enable devices in your fleet to interact securely with your Chef Server. It includes Chef Knife, InSpec, Cook style, Habitat, and Test Kitchen. It also contains embedded Ruby and other dependencies, so you don’t have to install anything else to get started with Chef tools.
Setting up the Environment
Chef Client
Download and install Workstation. Verify the installation in your terminal with the command.
$ chef –v
Create a directory for your encrypted data bag
$ mkdir data_bag/accounts
Create a data bag item for an account that you want to encrypt
$ subl data_bag/accounts/google-id.json
{
"id": "google-id",
"email": "akshay@gmail.com",
"password": "akshay123"
}
Create the data bag on the Chef server
$ knife data bag create account
Created data_bag[account]
Upload your data bag item to the Chef Server. The data will be encrypted as it is being transferred to the Chef server.
$ knife data bag from file accounts google-id.json --secret ‘decryptdata’
Updated data_bag_item[account::google-id]
‘decryptdata’ is the key that will be used to decrypt the encrypted data from the Chef server.
The encrypted data bag items can be accessed from the recipes. However, the secret key is hardcoded which can be a security vulnerability.
google_account = Chef::EncryptedDataBagItem.load("accounts", "google-id", "decryptdata") google_account [“password”] # will give you the decrypted password.
If you don’t want your --secret command to show up on your shell history or your log files, you can use a private key instead of plain text. This can also be used instead of hard coding the secret key into your recipes.
$ knife data bag from file accounts google-id.json --secret-
file .chef/private_key.pem
create an openssl format private key like this
$ openssl genpkey -algorithm RSA -aes-256-cbc -outform PEM -
out private_key.pem -pkeyopt rsa_keygen_bits:2048
The next step is to verify that your data bag items are encrypted.
$ knife data bag show accounts google-id
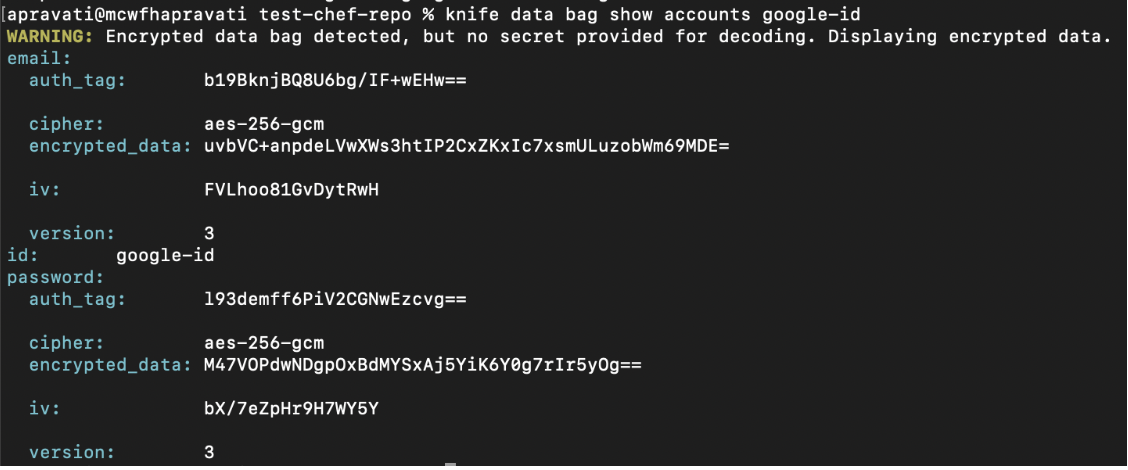
You can decrypt the data by providing the secret key or by passing the key file.
$ knife data bag show accounts google --secret 'decryptdata'

If you provide the wrong key file or secret key, an error message will appear
$ knife data bag show accounts google --secret 'Open sesame!'
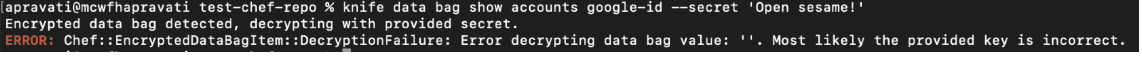
Passing the secret key to the knife command creating the data bag item encrypts the contents of the data bag. Chef uses the shared secret to encrypt and decrypt data bag items. Everyone having access to the shared secret will be able to decrypt the contents of the encrypted data bag item.

