As the environments we manage grow, so too does the potential risk to our systems as new vulnerabilities and exploits seem to crop up on a regular basis. As such, a question folks frequently ask is, “how can I use Chef to apply patches to the systems I manage?” The short answer is, very easily; updating systems isn’t a particularly difficult task in and of itself, it’s implementing a process that does so safely and verifiably that takes some planning.
Below is a recording of a webinar I recently presented on this topic. In it, we discuss not only the “how”, but the “why” of patching. If our intention is to mitigate risk in our environments, we can only do so if we explicitly and individually acknowledge those risks, and have a way to address each with confidence.
Let’s take a quick review of the risks covered in the webinar, how Chef can help you address then, and close with some follow-on activities you can do to start automating in your environment!
The risk of leaving environments unpatched
Does your organization have a way of determining how many systems have uninstalled updates? How often is that evaluated? Where is that data collected? These are some of the first questions we need to answer, because if we don’t have solid insight into the current makeup of our estate, we have no way to evaluate the cost and effort required to update it. Similarly, if we’re not checking our systems on a frequent cadence, that information can be out of date before we know it.
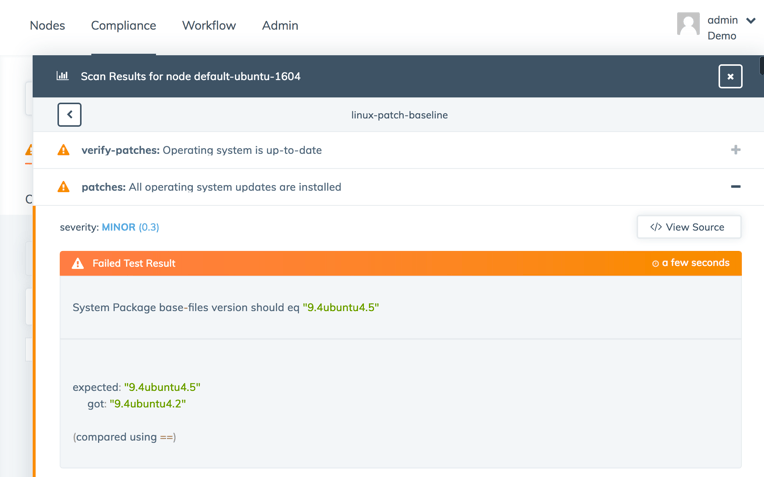
With InSpec and the audit Cookbook, we have the ability to evaluate those baselines as often as our machines check in with Chef. With Chef Automate, we can view aggregate as well as per-server historical data to make sure we can get all the information we need whenever we need it.
The risk of patching our environments
Even after you identify systems in need of patching, it has historically taken a long time to apply those patches. Verizon’s 2017 Data Breach Investigations Report found that most organizations remediate identified patching issues within 12 weeks, roughly in line with a quarterly patching cycle. The pain of these long turnarounds is keenly felt across the industry, and as our environments and our customers’ reliance on them continue to grow, ultimately unsustainable.
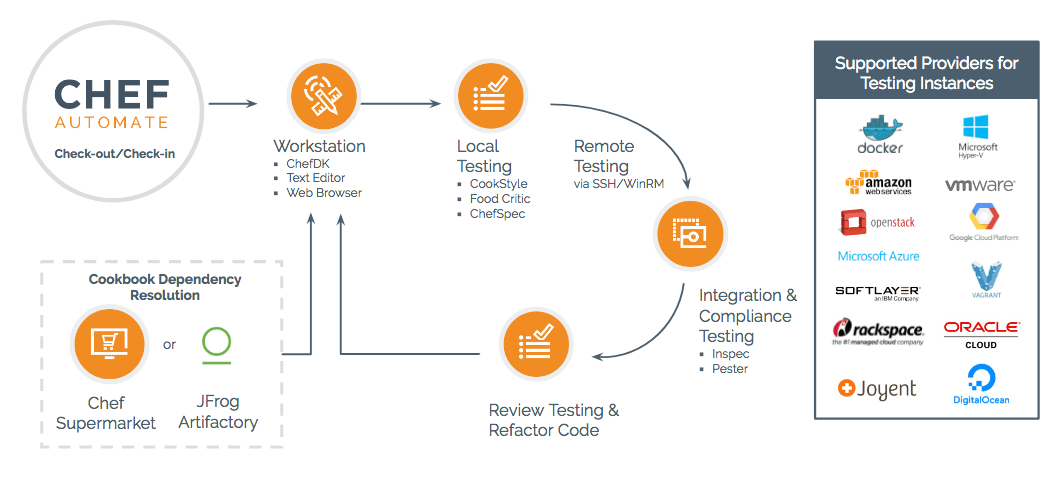
The ChefDK includes a suite of testing tools that will allow you evaluate new updates quickly in local and development environments. The Chef Server allows for organization of systems by environment and function, providing a means to evaluate changes in contained sub-sets of your estate. Finally, Chef Automate provides workflow tools that can help teams define a pipeline for evaluating the impact of new updates on their mission critical applications so that they can be released with confidence and velocity.
The risk of incomplete patching
The final risk to cover is that of uncaptured failure. Patching a dozen systems is relatively straightforward. Patching tens of thousands, less so. When we increase scale, we also increase chances of missing systems as we look to increase our update cadence.
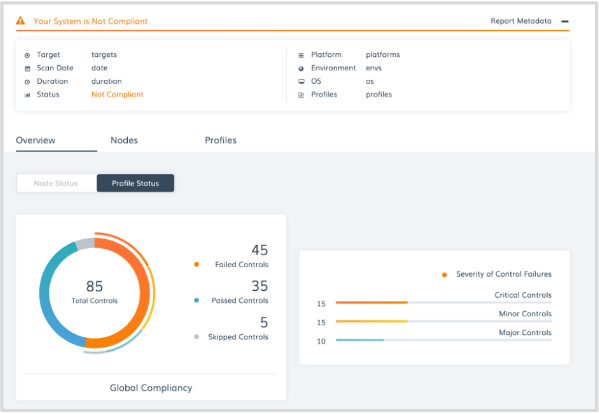
Chef helps ensure that updates are applied consistently to all of our servers, and Chef Automate gives us a dashboard where we can confirm those updates were applied successfully, and notify us when and if an issue arises. In concert with the same audit Cookbook used to identify systems in need of patching, we have everything we need to both ensure our patches were applied, and that none have been missed in the process.
What’s next?
We hope you enjoyed this presentation! As ever, join us in Community Slack to talk shop, and if you’d like to learn more about implementing Chef Automate in your organization, drop a line to sales@chef.io and we can set up a call to discuss how Chef can help you drive the outcomes your business demands.
For some hands-on experience with Chef Automate and InSpec, please check out the Integrated Compliance track on Learn Chef Rally. The compliance profile used in this webinar was the Dev Sec Linux Patch Baseline, and there is a corresponding Windows Patch Baseline as well. Finally, check out the Chef Supermarket for some great cookbooks for managing popular public repositories, or working with other package management tools like Redhat Satellite or WSUS.

