Update [8-June-2023] - Chef Automate version 4.7.52 and above will have the updated Go Lang version (1.19.3).
A new version of Chef Automate will be released in the early June 2023, which includes an upgrade to Golang 1.19. This change is required since the existing version of Golang and Go's standard libraries are no longer supported.
Please keep reading to determine if this change will impact you.
What is the Change?
Automate is moving the product builds from Golang version 1.15 to 1.19 to keep the language features up to date. Please refer to Go 1.15 Release Notes for more information.
The updated version of Chef Automate, to be released in the early June 2023, will update the core build framework of Golang to 1.19.
The change in the Golang version will impact the custom certificates used for interaction with external systems. The common name field of X.509 certificates will no longer be considered the hostname when the Subject Alternative Name (SAN) is absent.
Why the Change?
Who is impacted?
Customers using Automate or Automate HA with custom certificates generated with OpenSSL 1.1.1, or above which do not have the Subject Alternative Name (SAN) field will be affected by this upgrade. Automate or Automate HA may stop working if you upgrade to this version without updating the certificates.
What is the Impact?
Some changes that may be observed:
- Automate and Automate HA will not work correctly with custom certificates and will throw errors.
- Automate and Automate HA will not be able to communicate
with an externally deployed database, both PostgreSQL and OpenSearch.
- Automate and Automate HA will stop interacting with external services for the data feed service and/or notification service.
- Automate and Automate HA may behave unpredictably with external web services.
Check if You are Impacted
Please check certificates installed on Automate, external databases and web services to ensure that the Subject Alternative Name (SAN) has the correct value.
- In case of an external open search please refer to the opensearch.yml file to find the location of the certificate. In most Linux distributions, the file is available at /etc/opensearch/opensearch.yml.
- In the case of external PostgreSQL, by default,
your certificate will reside at $PGDATA/server.crt.
- In the case of Automate frontend load balancer, the certificate is available at /hab/svc/automate-load-balancer/data/ location.
1. To check mycert.cer, please run this command:
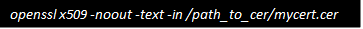
2. The output of the command will look like this:

3. Look for the “X509v3 Subject Alternative Name
" field in the output, as shown above.
If you do not see a value for the "X509v3 Subject Alternative Name", you ARE impacted.
What Should You Do if You are Impacted?
An OpenSSL CSR with the SAN should have the following attributes:

Once your custom certificate is updated, you must re-apply it.
-For Standalone Automate use the config patch to apply the load balancer certificate.
-There will be downtime while applying the updated certs to an externally managed databases or with custom certificates provided for the Automate frontend load balancer.
Are You Facing Issues During This Process?
Upgrade Chef Automate documentation: https://docs.chef.io/automate/upgrade/

