Celebrate Cybersecurity Awareness Month with a Lesson on Zero Trust.
The traditional approach to securing corporate information resources assumed several things:
- Every endpoint being used to access resources was owned, issued and managed by the enterprise.
- All users, devices and applications were in fixed and predictable locations, usually on a corporate network behind a firewall.
- A single method of verification at the point of initial access was sufficient.
- Corporate-managed systems with the same classification could all inherently trust one another.
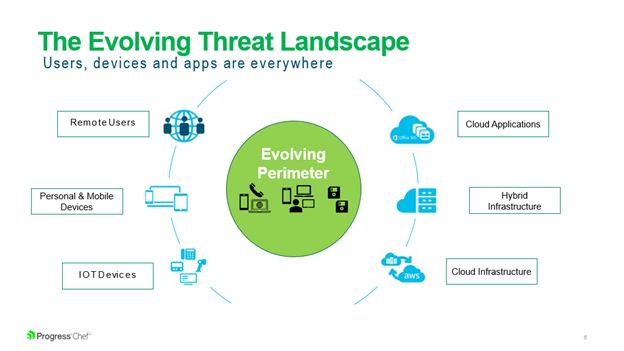
Threats are Everywhere
Cyber criminals are getting better every day at attacking IT infrastructure. Many of these exploits are created by a hacker and then spread to others through the Internet. Many attacks can even be bought for peanuts as a service. Meanwhile with the dramatic increase in mobile and remote work, the Internet of Things (IoT), not to mention the bevy of new applications, services and equipment, the attack suface is ever widening.
What is Zero Trust?
Zero Trust security is an IT security model that requires strict identity verification for every person and device trying to access resources on a private network, regardless of whether they are sitting within or outside the network perimeter. No single specific technology is associated with Zero Trust; it is a holistic approach to network security that incorporates several different principles and technologies.
The DevOps Angle
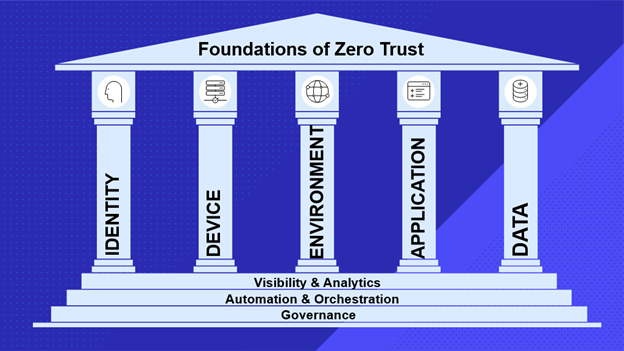
While the foundations of Zero Trust are well known – identify, device, environment, application and data – it’s interesting to think about Zero Trust in the context of DevOps principles, including visibility and analytics, automation and orchestration and governance.
“The first basic principle is to authenticate and verify access tool resources. Each time a user accesses a file share and application or cloud storage device, we need to re-authenticate that user's access to the resourcing question. You have to assume that every attempt and access to your network is a threat until confirmed otherwise, regardless of location or access or hosting model,” said Rick Brown, Principal Sales Engineer for Progress Chef. “To implement this set of controls, row authentication and access protocols, premise security and network access controls, the least privileged access concept is a security paradigm that limits each user's access to only the access they need to do their job. By limiting each user's access, you prevent an attacker from gaining access to a large amount of data with a single compromised account.”

Rick Brown, Principal Sales Engineer for Chef
DevOps Zero Trust Best Practices
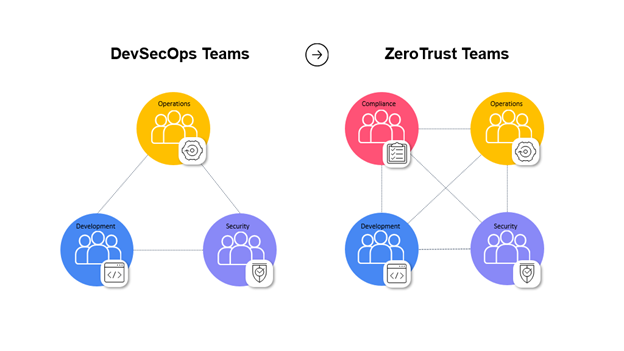
These efforts move from the triangular DevSecOps approach that includes DevOps and security to include a fourth dimension: compliance.
Chef and Zero Trust
- Establishing the Trust: The devices that are within the network are identified and checked. Then a local agent is installed which gives regular status of the devices from time to time. After installing this local agent, one can establish trust with that device by checking the device context and identity, the health and status alongside all the relevant attributes like the compliance state and so forth.
- Enforcing Trust Based Access: Just because a local agent has been installed within the device doesn’t mean that the user of that particular device gets to access everything within the server. There are certain limitations imposed over the network – like applications that can only be accessed by connecting to the VPN. Limitations based on the types of work are also imposed on the users. The users are granted access to those applications and resources which are needed based on his/her job profile.
- Continuous Trust Verification: The users within the network are continuously verified from time to time. They are asked to change passwords and once changed the users are automatically logged out of their devices and asked to carry out the verification steps again. IT Managers can continuously keep an eye on the list of devices, along with their activity and behaviors. A unified dashboard to track the current status of nodes in terms of configuration, health and compliance makes it easier to track security and configuration management data across the entire IT resource fleet.
“The benefits of using these approaches include the prevention of network access and lateral movement using compromised or stolen credentials. It also offers a single pane of glass visibility to the entire fleet. We're talking about workstations here as well as what's in the production systems. It offers monitoring and inspection but doesn't interfere with the user experience for accessing applications,” said Jacob George, Product Manager for Chef.




